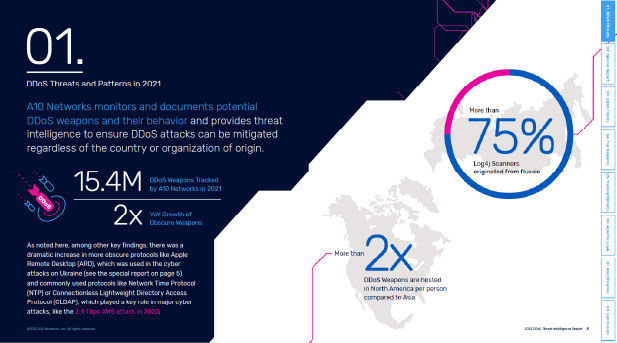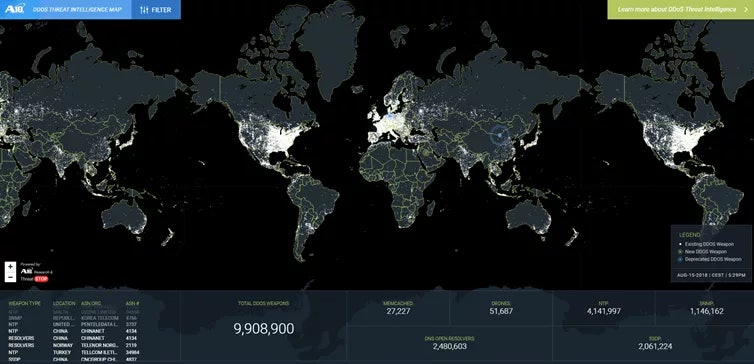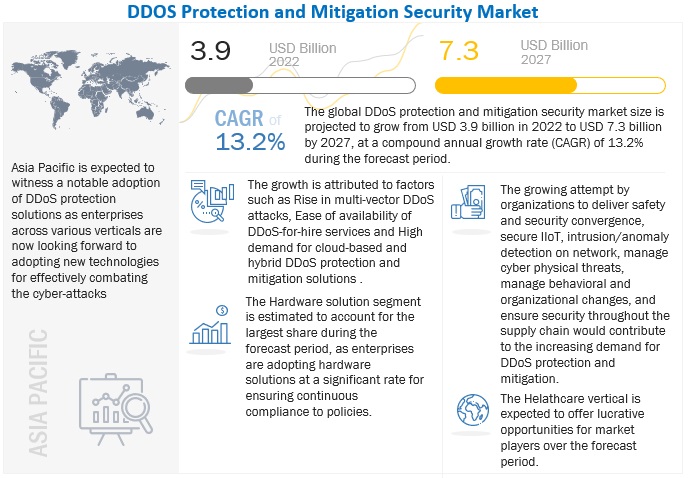
DDoS Protection and Mitigation Market Size, Share and Global Market Forecast to 2026 | MarketsandMarkets

Concerns Security | Distributed Denial of Service Attacks | Moral Issues, Societal Factors Security Although distributed computing looks to provide an efficient means of conducting extraordinarily large scale computations, there are numerous privacy and ...
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm

Game theoretic solution for an Unmanned Aerial Vehicle network host under DDoS attack - ScienceDirect

Drone demo shows it's possible to protect 5G-managed devices from DDoS, exfiltration attacks | Network World
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm
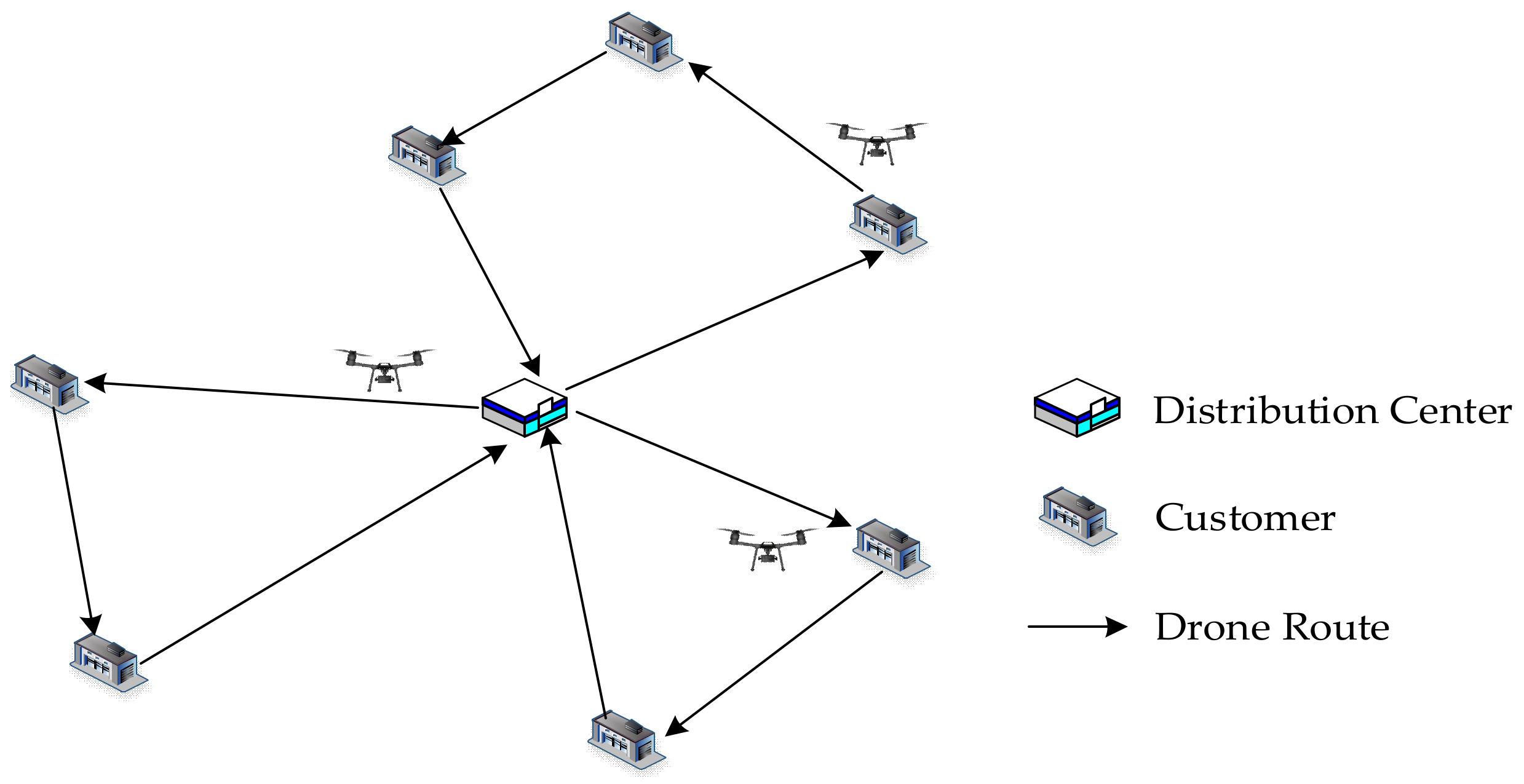
Sustainability | Free Full-Text | Optimal Model and Algorithm of Medical Materials Delivery Drone Routing Problem under Major Public Health Emergencies | HTML
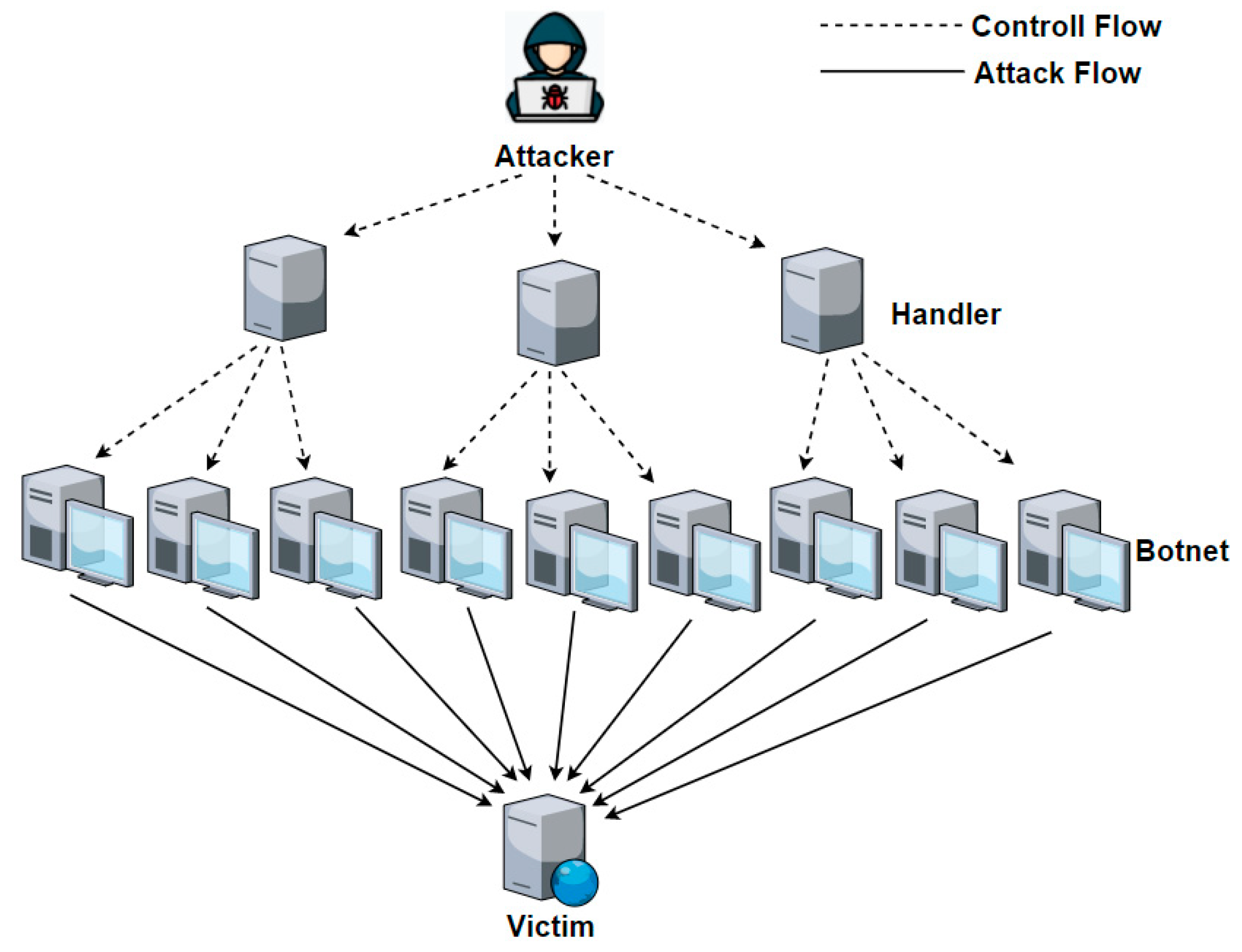



![Denial of service (DoS) attack [78] | Download Scientific Diagram Denial of service (DoS) attack [78] | Download Scientific Diagram](https://www.researchgate.net/profile/Phuoc-Dai-Nguyen/publication/349419829/figure/fig2/AS:1001946601238529@1615894093911/Denial-of-service-DoS-attack-78.png)